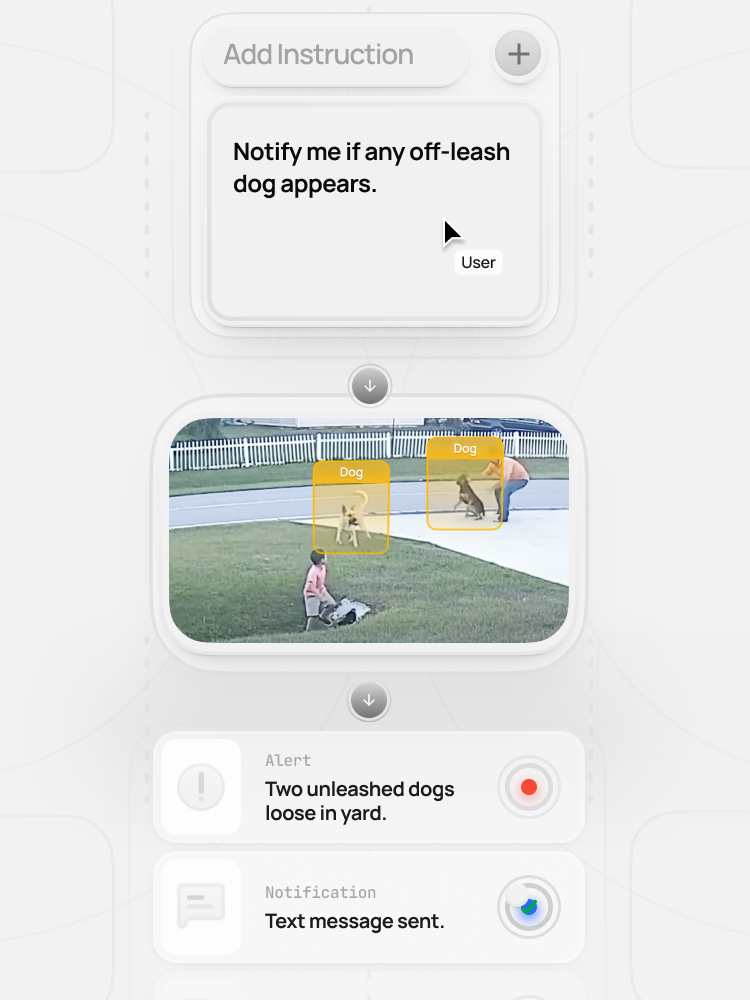
Prevent crime before it happens
The only AI surveillance agent with human-level contextual awareness, intelligent crime deterrence, and effortless setup: faster, smarter, and ready out of the box at a fraction of the cost.
Partnered with the World's Leading Tech Innovators.